Overview:
ClearPass OnGuard agents perform advanced endpoint posture assessments, on leading computer operating systems to ensure compliance is met before devices connect. Running on the Aruba ClearPass Policy Manager platform, the advanced network access control (NAC) framework in ClearPass OnGuard offers exceptional safeguards against vulnerabilities.
The following operating systems and versions are supported:
- Microsoft – Support for Windows 7 and above.
- Can be run as a service.
- Apple – Support for Mac OS X 10.7 and above.
- Linux – Support for Red Hat Enterprise Linux 4 and above, Ubuntu 12.x LTS and 14.x LTS, Community Enterprise Operating System (CentOS) 4 and above, Fedora Core 5 and above, and SUSE Linux 10.x.
Supported agents:
| |
OnGuard Persistent Agent |
OnGuard Dissolvable Agent |
Microsoft’s NAP Agent |
| Microsoft |
|
|
|
| Apple |
|
|
|
| Linux |
* |
|
|
Note: Auto-remediation only supported by persistent agents
* Persistent agent supported on Ubuntu endpoints running 12.x LTS or 14.x LTS
Automate health checks and posture assessments
In addition to system-wide per-session NAC protection, you can specify whether to allow or deny peer-to-peer applications or USB storage devices. Network access can be denied if storage is not encrypted and IT can be sure that laptops brought to the help desk have the latest patches and hot fixes.
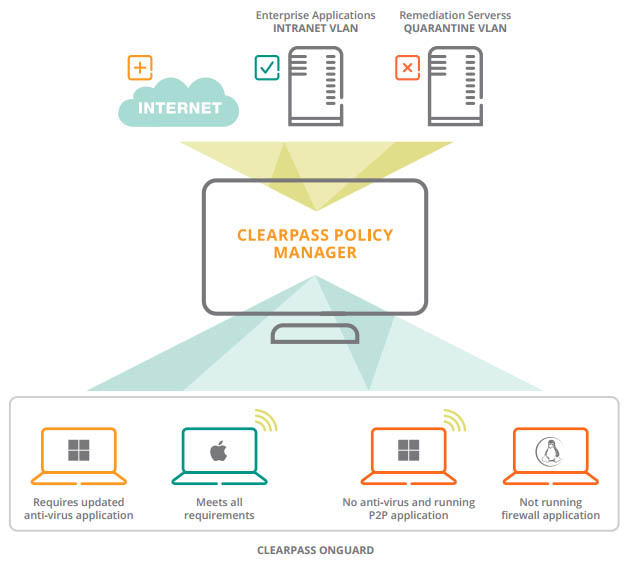
 Ensure device compliance before they ever connect
Ensure device compliance before they ever connect
You can automatically remediate or quarantine endpoints that are not in compliance with corporate posture policies. Using the administrator dashboard, it’s easy to keep an eye out for non-compliant devices, users, and the reasons for non-compliance.
BYOD and IT-issued devices
Persistent agents allow for automated remediation for IT-issued devices while BYOD and guests can use a dissolvable agent that’s automatically uninstalled once the device is cleared.
Operating system support
ClearPass OnGuard is capable of supporting a wide range of mobile device operating systems, including Windows, Mac OS X, and popular Linux versions.
Advantage:
In addition to anti-virus, anti-spyware and personal firewall audits performed by traditional NAC products, OnGuard agents can perform additional posture and health checks, to ensure a greater level of endpoint compliance.
Persistent and dissolvable agents
The difference between the two is that the persistent agent provides nonstop monitoring and automatic remediation and control. When running persistent OnGuard agents, ClearPass Policy Manager can centrally send system-wide notifications and alerts, and allow or deny network access. The persistent agent also supports auto and manual remediation.
Alternatively, the web-based dissolvable agent is ideal for personal, non IT-issued devices that connect via a captive portal and do not allow agents to be permanently installed. A one-time check at login ensures policy compliance. Devices not meeting compliance can be redirected to a captive portal for manual remediation.
Once the browser page used during authentication is closed, the dissolvable agent is removed leaving no trace.
Automatic remediation
If unhealthy endpoints do not meet compliance requirements, the user receives a message about the endpoint status and instructions on how to achieve compliance if auto-remediation is not used.
Messages can include reasons for remediation, links to helpful URLs and helpdesk contact information. ClearPass persistent agents provide the same message and remediation capabilities for 802.1X and combined environments.
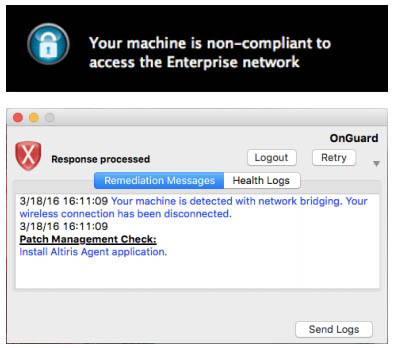
Persistent and dissolvable agents can be used for endpoint health checks.
IT-managed and BYOD endpoint compliance
OnGuard persistent and dissolvable agents can be used together in environments where endpoints are owned by the organization, employees and visitors. This ensures that all devices are assessed and granted proper privileges before accessing the network.
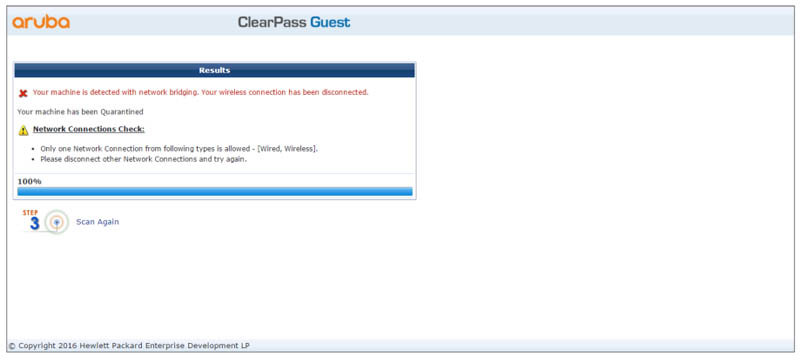
Detailed Mac OS X quarantine messages.
Complete endpoint visibility
To simplify troubleshooting, endpoint control and compliance reporting, ClearPass Policy Manager offers the ability to centrally managed health-check settings and policies. Views of ClearPass OnGuard activity, including user and device data show information about each device that connects using OnGuard agents.
Centralized view of endpoints OnGuard activity.
Real-time endpoint compliance
Depending on operating system type OnGuard performs the following level of posture and health checks.
| |
Windows |
Mac OS X |
Linux |
| Installed Applications |
|
|
|
| AntiVirus |
|
|
|
| AntiSpyware |
|
|
|
| Firewall |
|
|
|
| Disk Encryption |
|
|
|
| Network Connections |
|
|
|
| Processes |
|
|
|
| Patch Management |
|
|
|
| Peer to Peer |
|
|
|
| Services |
|
|
|
| Virtual Machines |
|
|
|
| Windows Hotfixes |
|
|
|
| USB Devices |
|
|
|
| File Check |
|
|
|
* Chart represents ClearPass version 6.6 functionality.
** Disclaimer: Not all checks are supported across operating systems and agent type.
Solutions:
Security Considerations for Next Generation Network Access and Endpoint Compliance
The dangers of endpoints connecting to the network before scanning for device health. Endpoint compliance assessments are critical for today’s mobile workforce environment. Employees, contractors, and guests treat IT-issued laptops as if they own them. Meanwhile, bring your own device (BYOD) has become popular due to convenience, cost savings and IT offload. Unfortunately, user behavior and connecting these devices to enterprise networks is a growing concern that adds potential threats.
Legacy network access control (NAC) required IT to install supplicants and agents on IT-issued computers to ensure the latest A/V software was updated and scanned. Next generation endpoint compliance allows for the automation of configuring devices, with little IT hassle, with improved policy creation and enforcement. Endpoint type will include laptops and desktops, smart phones, and tablets.
In this paper, we’ll discuss how and where new generation endpoint compliance should be enforced as well as additional considerations that are critical for ensuring a secure network.
NAC Re-Invented
Early issues with deploying NAC are a thing of the past — in fact, there’s no longer a need to distribute supplicants. Devices come with usable supplicants and the distribution of agents is automated today.
Next generation endpoint compliance is “IT lite” because agents can be automatically pushed to the client. Today’s NAC solutions are typically used to distribute agents to computers and enterprise mobile management (EMM) solutions are used for distributing agents to smart phones and tablets. In both scenarios, the policy management component within a NAC solution will be used to enforce network access privileges. The goal is to perform the assessment before full access privileges are granted.
This ease of deployment has lifted a significant burden off of IT that otherwise would have hampered implementation. More importantly, today there are many features that are available within a NAC solution that solve the security implications of a mobile workforce.
Basic Features of an Endpoint Compliance Solution
Today, endpoint compliance means much more than just checking for traditional anti-virus and firewall status. IT can now require and control the use of many more variables that have been implicated in breaches. This can include controlling USB ports, P2P file share blocking, spyware updates, patch/hotfix management, and more.
Additionally, today’s NAC solutions can be configured so that features run in the background. Real-time assessments can trigger auto-remediation to change the status of an endpoint that makes it non-compliant. When auto-remediation is not an option, the NAC solution can also communicate instructions to the end user on how to resolve non-compliance issues via SMS, email, or a service desk call.
Tying these features together with the AAA capabilities of a policy solution allows for much more granular and robust policies that can leverage the detailed user and device context that’s available today. Device fingerprinting, the status of a certificate or credentials and user location data can now be collected and used to determine if a device should be connected to a network.
This simplifies IT involvement and improves the end user experience as self-management of their devices makes it easier to comply with changing policy requirements.
Differences Between NAC Solutions
Not all NAC solutions are equal. Most importantly, when approaching access control with a security mindset, when device health checks occur is often the most overlooked gap.
From a security standpoint, the strength of your defenses is inversely proportional to end user and/or IT convenience. Sometimes a “good enough” approach is fine – for example, some websites do not require lengthy or complicated passwords, but more important accounts, such as brokerage accounts, may require strong passwords and two-factor authentication. However, in the case of endpoint compliance and health checks in the mobile world, slightly more involved challenges are needed considering the implications of a large breach, data loss, or infected network.
The convenience first, security second school of thought for some vendors is to let the device onto the network before doing a policy or health check. And instead of using 802.1X, RADIUS and other authentication and enforcement protocols, they attempt to scan devices after they’ve been granted a connection to the network. This way, elements of the device can be scanned faster than if an agent were issued to a device and securely scanned and authenticated first.
Although the time increment may be small before detecting a threat in this model, it can be just enough time to expose your network to malicious code or data loss than if enforcing an assessment and authorization before the device acquires an IP address. In other words, merely allowing a device to acquire an IP address first and then scan packets, still allows for enough time to compromise your network.
Furthermore, the speed with which a device can be scanned before acquiring an IP address is negated by the intrusive performance hit a device will take while the end user is working on an application. The size of an organization is another consideration. Devices farther away from where the NAC solution sits, will have access to resources longer than may be desired.
Trusting the device before enforcing compliance policies is akin to locking your front door when you leave for work in the morning — after leaving the door open overnight. You are leaving yourself vulnerable at the most critical and vulnerable time. The same is true for endpoint control. It makes sense to enforce a policy before allowing untrusted devices onto the network. Just because devices are known does not mean that they should be trusted.
Implications of the Pre-Enforcement Access Model
Stories about breaches and corporate data loss are increasingly all over the news feeds. Some of the largest companies in the world have had to disclose devastating breaches because someone brought a device onto the network that was not IT issued and logged into the network without a health check. Once malicious code is injected into the network in the fraction of a second that the user logs in, there is virtually no way to stop the propagation of the infection throughout the network – the damage has already been done. And now with laws requiring public disclosure and notification of breaches, the costs are staggering – not to mention the potentially personal legal implications for C-level executives.
Pre-Health Check vs. Post-Health Check
Although accessing the network after checking for device health policy is critical from a security standpoint, both pre and post assessment and enforcement is ideal for strong security. Say you have a pre-enforcement solution and policy in place and a remote employee wants to use their personal laptop on the network. They are required to download an agent which then scans for a policy. If the device is clean, they are allowed onto the network. If there is an anti-virus program that is outdated, it can be auto-remediated.
But, what if a user does something after they are on the network? Say they click on a malicious link that circumvents their current anti-virus application by turning off their firewall. A persistent agent will continue to check the device and will either auto-remediate or block the user from the network if a firewall is a component of the IT policy. If there was no persistent agent, there would be no way to auto-remediate or flag and block any changes to the device post device health check.
Aruba ClearPass - A Security Centric Endpoint Compliance Solution
Aruba ClearPass OnGuard, a component of the Aruba ClearPass Policy Management Platform can be used to perform device assessments on any computer or laptop connecting to the network. The Policy Manager is also capable of pulling attributes from an EMM system to ensure that only compliant smartphones and tablets are connected to Wi-Fi and wired networks.
With the use of a persistent agent, IT can check for anti-virus, spyware, firewalls, hot fixes and more in real time before granting authorization privileges onto the network. If there is a service or requirement that can’t be auto-remediated, for example, if disk encryption must be enabled, the user can be notified that they can’t access the network and must restore their encryption before they will be connected to the network.
Not only will ClearPass ensure non-IT issued laptops and computers are compliant before they are allowed network access, but they can do so in an “IT lite” fashion on both the wired and wireless network before an IP address is issued.
A lightweight dissolvable web based agent is also available for users segmented on a less critical segment of the network, for instance, a guest network. Personal devices do not allow agents to be permanently installed in most cases and would connect through a captive portal that uses a native dissolvable agent. The dissolvable agent is completely removed from the device once the browser is closed.
Ordering Guidance:
ClearPass OnGuard can be ordered via dedicated OnGuardonly subscription that includes ArubaCare support or perpetual licenses. Available enterprise options enable organizations to flexibly use the licenses for ClearPass OnGuard, Onboard or Guest.
Ordering ClearPass OnGuard involves the following three steps:
- Determine the number of unique computer endpoints that will have posture/health checks performed prior to network access within your environment.
- Choose the appropriate ClearPass Policy Manager hardware or virtual appliance to accommodate the total number from above. The Enterprise Starter Bundle that contains 25 licenses can be used.
- Select the remaining capacity needed to accommodate the total number of endpoints using the OnGuard part numbers. Anything over the capacity of a base appliance will require the purchase of a second ClearPass Policy Manager appliance.
Example: To support the provisioning of 2,000 devices, make sure that ClearPass Policy Manager is sized to accommodate 2,000 endpoint devices.
Purchase the following:
- ClearPass Appliance – CP-HW-5K or CP-VA-5K
- ClearPass OnGuard – 2 X LIC-CP-OG-1K or for subscription, SUBX-CP-OG-1K
Additional ClearPass OnGuard capacity can be purchased at any time to meet growth demands. ClearPass OnGuard is licensed on a per client basis.


 Ensure device compliance before they ever connect
Ensure device compliance before they ever connect



