Overview:
Aruba ClearPass Policy Manager provides role- and devicebased network access control for employees, contractors and guests across any multivendor wired, wireless and VPN infrastructure. With a built-in context-based policy engine, RADIUS, TACACS+ protocol support, device profiling and comprehensive posture assessment, onboarding, and guest access options, ClearPass is unrivaled as a foundation for network security in any organization.
For wider security coverage, using firewalls, EMM and other existing solutions, ClearPass Exchange allows for automated threat protection and workflows to third-party security and IT systems that previously required manual IT intervention.
In addition, ClearPass supports secure self-service capabilities for end user convenience. Users can securely configure their own devices for enterprise use or Internet access. Aruba wireless customers can provide registration of AirPlay-, AirPrint-, DLNA-, and UPnP-enabled devices for sharing.
The result is a comprehensive and scalable policy management platform that goes beyond traditional AAA solutions to deliver extensive enforcement capabilities for IT-owned and bring-your-own-device (BYOD) security requirements.
Key Features
- Role-based network access enforcement for multivendor Wi-Fi, wired and VPN networks.
- Industry-leading performance, scalability, high availability and load balancing.
- Intuitive policy configuration templates and visibility troubleshooting tools.
- Supports multiple authentication/authorization sources (AD, LDAP, SQL dB) within one service.
- Self-service device onboarding with built-in certificate authority (CA) for BYOD
- Guest access with extensive customization, branding and sponsor-based approvals.
- Supports NAC and EMM/MDM integration for mobile device assessments.
- Comprehensive integration with third party systems such as SIEM, Internet security and EMM/MDM.
- Single sign-on (SSO) and Aruba Auto Sign-On support via SAML v2.0.
- Advanced reporting of all user valid authentications and failures.
- Built-in profiling using DHCP and TCP fingerprinting.
- Hardware and virtual support for ESXi and Hyper-V appliances.
- Automatic cluster upgrade.
The ClearPass Difference
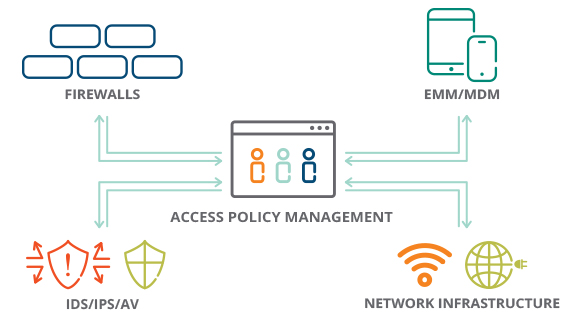
The ClearPass Policy Manager is the only policy solution that centrally enforces all aspects of enterprise-grade mobility and NAC for any industry. Granular network access enforcement is based on a user’s role, device type and role, authentication method, EMM/MDM attributes, device health, location, and time-of-day. ClearPass offers extensive multivendor wireless, wired and VPN infrastructure support which enables IT to easily rollout secure mobility policies across any environment. Deployment scalability supports tens of thousands of devices and authentications which surpasses the capabilities offered by legacy AAA solutions. Options exist for small to large organizations, from local to distributed environments.
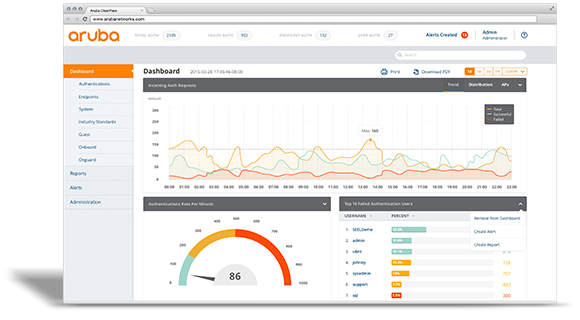
Advanced Reporting and Alerting with Insight
Policy Manager includes advanced reporting capabilities that includes customizable dashboards for authentication, endpoint profiling, industry standards, and other information for guest, onboarding, and device health, all in an at-a-glance dashboard. InSight also includes granular alert capabilities.
Features:
 Smart policies with mobility and IoT in mind
Smart policies with mobility and IoT in mind
ClearPass solves today’s digital workplace security challenges across any multivendor wired or wireless network by replacing outdated legacy AAA with context-aware policies. It delivers visibility, policy control and workflow automation in one cohesive solution.
Industry-leading visibility and device profiling that’s built-in
ClearPass profiling classifies all mobile and IoT devices to define smart policies that determine access to wired and wireless networks. You can automatically grant or deny user access privileges based on device type, ownership status or operating system.
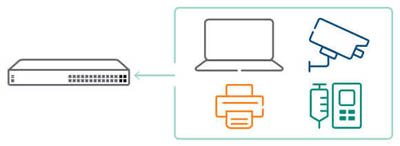 Futureproof your existing network infrastructure
Futureproof your existing network infrastructure
Leverage your existing third party security solutions – perimeter firewall, SIEM, and MDM — to integrate contextual user information with ClearPass. And with OnConnect, use existing switch protocols for visibility, access controls and enforcement of computers and IoT devices.
Integrate and share with third-party IT systems
ClearPass Exchange is the central hub that shares contextual data with a wide range of third-party IT systems – firewalls, MDM/EMM and SIEM – for end-to-end policy enforcement and visibility. ClearPass supports data exchange via APIs, Syslog messaging, and our new ClearPass Extensions.
Real-time analytics
Learn how ClearPass Insight provides real-time analytics and reporting to better understand who and what is on your network, so you can resolve issues quickly.
Secure BYOD
Employees are bringing more and more personal devices to work. In turn, IT relies on ClearPass Onboard for an easy and automatic way to configure the process, making sure all devices are secure.
Advanced Policy Management
Enforcement and visibility for wired and wireless
With ClearPass, organizations can deploy wireless using standards-based 802.1X enforcement for strong authentication. ClearPass also offers a way to create non- .1X policies on wired networks with OnConnect – for those organizations not ready to go full 802.1X and AAA throughout their wired infrastructure. ClearPass allows for a hybrid approach to enable IT to gain insights about all devices – computers, smartphones and IoT – accessing the network. Concurrent authentication methods can be used to support a variety of use-cases. It also includes support for multifactor authentication based on login times, posture checks, and other context such as new user, new device, and more. Attributes from multiple identity stores such as Microsoft Active Directory, LDAP-compliant directory, ODBC-compliant SQL database, token servers and internal databases across domains can be used within a single policy for finegrained control. Contextual data from these profiled devices allows for IT to define what devices can access either the wired, VPN, or wireless network. Device profile changes are dynamically used to modify authorization privileges. For example, if a Windows laptop appears as a printer, ClearPass policies can automatically revoke or deny access.
Secure device configuration of personal devices
ClearPass Onboard provides automated provisioning of any Windows, Mac OS X, iOS, Android, Chromebook, and Ubuntu devices via a user driven self-guided portal. Required SSIDs, 802.1X settings and security certificates are automatically configured on authorized devices.
Customizable visitor management
ClearPass Guest simplifies workflow processes so that receptionists, employees and other non-IT staff can create temporary guest accounts for secure Wi-Fi and wired Internet access. Self-registration, sponsor and bulk credential creation supports any guest access need – enterprise, retail, education, large public venue.
Device health checks
ClearPass OnGuard, leveraging OnGuard persistent and dissolvable agents, performs advanced endpoint posture assessments over wireless, wired and VPN connections. OnGuard health-check capabilities ensure compliance and network safeguards before devices connect.
Additional Policy Management Capabilities
Integrate with security and workflow systems
ClearPass Exchange interoperability includes REST-based APIs, and forwarding of syslog data flows to and from ClearPass on-demand; that can be used to facilitate workflows with MDM, SIEM, firewalls PMS, call centers, admission systems, and more. For faster, flexible interoperability, ClearPass can allow end users to integrate container based extensions in real time for extremely fast interoperability with new partners or new features on-demand. Context is shared between each component for end-to-end policy enforcement and visibility.
Connect and work apps are good to go
ClearPass Auto Sign-On capabilities make it infinitely easy to access work apps on mobile devices. A valid network authentication automatically connects users to enterprise mobile apps so they can get right to work. Single sign-on (SSO) support works with Ping, Okta and other identity management tools to improve the user experience to SAML 2.0-based applications.
Solutions:
Access controls and visibility for any wired or wireless network
Remember when IT was the gatekeeper and ruled with a combination of strict policies and a fully-contained ecosystem? Those days are long gone. Today, billions of Wi-Fi-enabled smartphones, tablets and Internet of Things (IoT) devices are pouring into the workplace. Users are armed with more than three devices apiece and each device can have over 40 business and personal apps on it.
The use of IoT devices on wired and wireless networks has also challenged the model of pure IT management. Many of these devices are new technologies and will require access from external administration resources.
The expectation is that everything just works and is secure – in the office, at a branch or at home. As IT struggles to maintain control, they need the right set of tools to quickly program the underlying infrastructure and control network access for any unknown IoT and mobile device, without wasting countless hours and unnecessary resources. With the increasing variety and scale of apps running on the network, they need a common policy framework to move beyond perimeter-based security of the past.
Mobility and IoT are redefining todays security perimeter
The boundaries of IT’s domain now extends beyond the four walls of an enterprise. And the goal for organizations is to provide anytime, anywhere connectivity without sacrificing security. How does IT maintain visibility and control without impacting the user experience?
Understanding what devices are being used, how many, where, and which operating systems are supported provide a foundation. Deciding what happens when users and devices connect and when they are not in compliance is the key.
Organizations must plan for existing and unforeseen challenges. It’s not realistic to rely on IT and help desk staff to manually intervene whenever a user decides to work remotely or buy a new smartphone. Organizations need to adapt to today’s evolving devices and their use – whether a smartphone or surveillance camera.
 One place to manage all things
One place to manage all things
Aruba ClearPass takes a fresh approach to solving the security challenge – one that gives IT a simple way to build a foundation for enterprise-wide policies, strong enforcement, and an enhanced user experience. From this single ClearPass policy and AAA platform, contextual data is leveraged across the network to ensure that users and devices are granted appropriate access privileges – regardless of access method or device ownership. Policies include user roles, device types, available MDM data and certificate status, location, day-of-week, and time-of-day.
This enables consistent policy enforcement for an end-toend approach that siloed AAA, NAC, and guest solutions can’t deliver.
ClearPass Benefits
- Policies and AAA services that support any multivendor wireless, wired, and VPN environment.
- Network privileges based on real-time contextual data – user roles, device types, location, and time-of-day.
- Built-in device profiling that identifies device types and attributes for everything that connects.
- Real-time troubleshooting tools that help solve connectivity and user issues quickly.
- Built-in integration that allows you to build a coordinated defense where everything – third-party security solutions like MDM/EMM, firewalls and SIEM tools – work as one solution.
- The latest enhancements enable custom profiles to be created to identify and secure IoT devices in real-time, with minimal hands-on IT interaction.
- Integration with popular multi-factor authentication platforms for any network or application access.
Building a solid baseline
Tackling mobility starts with managing how users and their devices connect – wired, wireless or VPN – to access corporate resources. User roles, device risk-profiles, and other contextual data provide for granular policies that truly let you offer differentiated access.
ClearPass provides important features that make mobility easy:
- Role-based policy management for users and devices (IT- managed, BYOD, and IoT).
- Enterprise-grade AAA, including RADIUS/TACACS+ and 802.1X.
- A full suite of customizable captive portal options for guest access, BYOD, and sharing of resources using Bonjour and DLNA services.
- Complete visibility features – real-time dashboards and post authentication reporting.
ClearPass lets you leverage user and devices roles, dynamic VLAN and access control list (ACL) enforcement rules and services that touch everything from identity stores to Aruba and multivendor network infrastructure using standardsbased protocols.
The ability to utilize multiple identity stores within one service, including Microsoft Active Directory, LDAP-compliant directories, ODBC-compliant SQL databases, token servers, and internal databases sets ClearPass apart from legacy solutions.
Device provisioning without IT involvement
Managing the onboarding of personal devices for BYOD deployments can put a strain on IT and help desk resources, and can create security concerns. ClearPass Onboard lets users configure devices for use on secure networks all on their own. Unique device certificates even eliminate the need for users to repeatedly enter login credentials throughout the day. That convenience alone is a win. The additional security gained by using certificates is a bonus.
The IT team defines who can onboard devices, the type of devices they can onboard, and how many devices each person can onboard. A built-in certificate authority lets IT support personal devices more quickly as an internal PKI, and subsequent IT resources are not required.
Guest access that’s simple and fast
BYOD isn’t just about employee devices. It’s about any visitor whose device requires network access – wired or wireless. It requires a simple model that automates and simplifies the provisioning of network access for guests, but also provides expansive security features that keep enterprise traffic separate from guest traffic.
ClearPass Guest makes it easy and efficient for employees, receptionists, event coordinators, and other non-IT staff to create temporary network access accounts for any number of guests per day. MAC caching also ensures that guests can easily connect throughout the day without repeatedly entering credentials on the guest portal.
Self-registration takes the task away from employees and lets guests create their own credentials. Login credentials are delivered via printed badges, SMS text, or email. Credentials can be stored in ClearPass for set amounts of time and can be set to expire automatically after a specific number of hours or days. ClearPass also enhances the guest experience by enabling organizations to create branded guest portals that are sized for laptops and smaller mobile devices.
When device health determines access
During the authorization process, it may be necessary to perform health assessments on specific devices to ensure that they adhere to corporate anti-virus, anti-spyware, and firewall policies. Automation motivates users to perform an anti-virus scan before connecting to the enterprise network.
ClearPass OnGuard features built-in capabilities that perform posture-based health checks to eliminate vulnerabilities across a wide range of computer operating systems and versions.
ClearPass also provides advanced health checks that provide extra security:
- Handling of peer-to-peer applications, services, and registry keys.
- Determination of whether USB storage devices or virtual machine instances are allowed.
- Managing the use of bridged network interfaces and disk encryption.
Whether using persistent or dissolvable clients, ClearPass can centrally identify compliant endpoints on wireless, wired, and VPN infrastructures.
Getting more from third-party solutions
ClearPass Exchange lets you automate mobile security using popular third-party security solutions like firewalls, MDM/EMM, and SIEM tools. Leveraging the context intelligence that ClearPass contains allows organizations to ensure that security and visibility is provided at a device, network access, and traffic inspection and threat protection level.
Using a commom-language (REST) API, syslog messaging and a built-in respository called Extensions, automated workflows and decisions help simplify tasks and secure the enterprise – no more complex scripting languages and tedious manual configurations. And for faster integration, ClearPass container Extensions allows for flexible, real time integration with new third party features and partners.
ClearPass supports integration with popular multi-factor authentication (MFA) platforms for any network or application access. ClearPass offers a MFA challenge to mobile devices as they are onboarded to the existing network infrastructure for the first time and/or as they return for new connections. This MFA challenge can be presented to the end user based on different criteria in order to better satisfy corporate policy requirements: from certain locations, only for select mobile device types, or a select group of users.
With ClearPass Exchange, networks can automatically take corrective actions:
- MDM/EMM data like jailbreak status of a device can determine if it can connect to a network.
- Firewalls can accurately enforce policies based on user, group, and specific device attributes.
- SIEM tools can be setup to capture all authentication data for single dashboard visibility.
Network events can also prompt ClearPass Exchange to take action on the device by triggering actions in a bidirectional manner. For example, if a user fails network authentication multiple times, ClearPass can trigger a notification message directly to the device.
Access work apps securely from anywhere
Logging in to work apps throughout the day needs to be fast and effortless. The ClearPass Auto Sign-On capability does just that. Instead of a single sign-on, which requires everyone to login once manually to apps, ClearPass Auto Sign-On uses a valid network login to automatically provide users with access to enterprise mobile apps.
Instead of remembering and manually entering passwords for every work app, users only need their network login or a valid certificate on their devices. ClearPass can also be used as your identity provider (IdP) or service provider (SP) where Single Sign-On is utilized.
Bonjour, DLNA and UPnP services
Projectors, TVs, printers, and other media appliances that use DLNA/UPnP or Apple AirPlay and AirPrint, can be shared between users across your Aruba Wi-Fi infrastructure. ClearPass makes finding these devices and sharing between them simple.
For example, a teacher who wants to display a presentation from a tablet will only see an available display in their classroom. They will not see devices on the other side of the campus. They can also use the portal to choose who else can use the display – this keeps students from taking over the display.
Another example is within the healthcare sector – doctors can easily project digital PACS images from their iPads to a larger screen anywhere within a hospital. Patient collaboration just got simpler.
A Foundation for Security
Providing a seamless experience for today’s #GenMobile and the fast adoption of IoT technologies within the enterprise have created a host of new IT challenges. It takes planning, the right tools, and a strong foundation to secure anytime, anywhere access for mobile and IoT devices.
ClearPass solves these challenges by providing a platform that delivers policy control, workflow automation, and visibility from a single cohesive solution. By capturing and correlating real-time contextual data, ClearPass enables you to define policies that work in any environment – wireless, wired, or VPN.
The latest Aruba ClearPass enhancements also handle emerging network security challenges surrounding adoption of IoT, stronger mobile device and app authentication, and deeper visibility to security incidents. Automated threat protection and intelligent service features ensure that each device is accurately given network access privileges with minimal hands-on IT interaction.
Access Control Options for Wired Networks:
 When policy and access control are discussed, there’s usually an immediate association with wireless and unmanaged devices such as smartphones and IoT devices. As these devices are often used outside of the workplace and normally connect over the air, policy controls and device profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link.
When policy and access control are discussed, there’s usually an immediate association with wireless and unmanaged devices such as smartphones and IoT devices. As these devices are often used outside of the workplace and normally connect over the air, policy controls and device profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link.
As the modern workplace is full of external personnel such as temporary workers, contractors, and guests who may use their personal devices within the workplace, identity and device visibility have become valuable components during the authentication and authorization phase. This data is then used to enforce policies on wireless and wired networks. But, the growth of IoT devices, that are not associated with a specific user or group, is now causing security concerns on the wired network.
Without consistency on the wired network, malicious users can connect and access corporate resources easily. For instance, depending on the access switch configuration, users may be able to access the wired network through an authenticated device such as an IP phone’s built-in switch port. Even though there is some form of authentication, it may not necessarily apply to the devices connected through the IP phone.
This paper discusses options that bring wired networks closer to the same level of control that have been on wireless networks, regardless of access control method, either through secure means or non-AAA enforcement.
Option 1: Non-AAA Enforcement
With non-AAA enforcement, the goal on a wired network is to minimize the effort it takes to deploy a policy enforcement service. Endpoints do not require a supplicant or agent, which makes it convenient for laptops, printers, and IoT devices – many of which do not support an 802.1X supplicant. And, there is minimal configuration required on the actual switches.
When a device plugs into a wired port, the policy engine can be notified of the new device, and profiling techniques such as DHCP Fingerprinting or Windows Management Instrumentation (WMI) can be used to identify the type of device and the user. With this information, we can validate this device and user against the Active Directory or a device database so that appropriate policies can be applied to the switch port. This means that every device connecting to the wired network is profiled and evaluated providing much needed visibility.
Profiling consists of fingerprinting each device as well as the ability to perform device assessments to better understand the posture of a device. Methods of profiling and assessment include DHCP fingerprinting, SNMP scans, NMAP scans, Link Layer Discovery Protocol (LLDP), Cisco Discovery Protocol (CDP), Windows Management Instrumentation (WMI), and more. For Windows laptops, you can perform basic assessments like seeing if required services exist and if they are running on each device.
The advantage of using non-AAA enforcement is that there is minimal configuration, and it allows IT to quickly meet internal or external audit or compliance demands. You’re also able to build a comprehensive database of all devices connecting to the wired network, which becomes more important as IoT devices emerge in greater numbers.
Option 2: Identity-Based 802.1X Authentication
802.1X is the most secure option and provides real-time certificate or login and password based authentication. You also benefit by performing authentication before a device receives an IP address. In the non-AAA model, devices receive limited access to the network before any authentication.
Using 802.1X also provides better options for the authorization of device privileges. Instead of just VLAN placement, the use of ACLs, downloadable ACLs, and roles can be used to define access when the status of a device changes. The ability to use granular identity-based enforcement also makes it easier to share user information with firewalls and other security components for enhanced downstream policies and threat prevention. But as with anything related to security, there is an inverse relationship between convenience and the level of effort needed from IT to implement a model with secure policy management.
There are three components that must be in place and configured for 802.1X to work; a supplicant, an authenticator, and an authentication server. The supplicant resides on the endpoint device, the authenticator is the switch in a wired network, and the authentication server is a AAA component that typically uses the RADIUS protocol. In today’s world, the AAA server resides within a policy management solution.
For a wired environment, 802.1X eliminates port VLAN configuration issues as each device that connects can initiate a session for that specific connection. A user can’t unplug a printer, connect a laptop and gain access to the printer VLAN. The workflow, once a laptop is connected, would be to establish the identity of the user and device and perform a role-based enforcement for that user or device. Differentiated privileges can be granted based on user and device role, location, posture of the device, and more. For devices that do not support 802.1X, you can also use MAC address based authentication to enable connectivity to the wired network.
The profiling data that can be captured is similar to what can be collected in the non-AAA model, but enforcement options are greater as collected attributes can then be used to perform runtime changes of authorization based on changes of a device’s status.
Another advantage is that 802.1X supports logins and passwords, or the use of device certificates, which provide a higher level of security. Certificates can’t be spoofed. Today, onboarding services can automate the configuration of endpoint supplicants and create a database for use when performing authorization and enforcement. This can be used on wired, wireless and VPN networks to provide a consistent user experience.
Other advantages include the ability to change the privileges of connected devices based on their behavior. If multiple devices are connected behind a switch port, a change of authorization (CoA) to adjust security policies would not affect all devices, only the target device.
Recommendations
IT security administrators have spent a considerable amount of time securing the wireless network due to personal devices, guests, visitors, and contractors requesting Internet access. However, the wired network has often been overlooked due to lack of resources. Today, the growth of IoT and compliance requirements are driving the need for wired networks to receive the same level of attention.
Given that more and more security breaches are targeting IoT devices on wired networks, our recommendation is to deploy an option that makes sense for both wired and wireless networks. For this reason, Aruba ClearPass supports both non-AAA and secure 802.1X policy enforcement for wired, as well as wireless networks. ClearPass OnConnect allows for non-AAA wired enforcement so that customers can start down the policy and access control path. All devices can be profiled with user based authorization, all with minimal configuration on the switching infrastructure.
The more secure 802.1X enforcement model should be considered for greater policy enforcement options. As it will require more planning and configuration, if 802.1X is already being used for a wireless service, ClearPass provides mechanisms to unify policy enforcement across different network transport types, all from a single solution.
Specifications:
| Specifications |
| ClearPass Policy Manager Appliances |
- ClearPass Policy Manager is available as hardware or a virtual appliance that supports 500, 5,000 and 25,000 authenticating devices. Virtual appliances are supported on VMware ESX/i and Microsoft Hyper-V.
- ESX 4.0, ESXi 4.1, up to 6.0
- Hyper-V 2012 R2 and Windows 2012 R2 Enterprise
- Virtual appliances, as well as hardware appliances, can be deployed within an active cluster to increase scalability and redundancy.
|
| Platform |
- Built-in AAA services – RADIUS, TACACS+ and Kerberos
- Web, 802.1X, non-802.1X, RADIUS authentication and authorization
- Advanced reporting, analytics and troubleshooting tools
- External captive portal redirect to multivendor equipment
- Interactive policy simulation and monitor mode utilities
- Multiple device registration portals – Guest, Aruba AirGroup, BYOD, un-managed devices
- Deployment templates for any network type, identity store and endpoint
- Admin/Operator access security via CAC and TLS certificates
- IPSec tunnels
|
| Framework and protocol support |
- RADIUS, RADIUS CoA, TACACS+, web authentication, SAML v2.0
- EAP-FAST (EAP-MSCHAPv2, EAP-GTC, EAP-TLS)
- PEAP (EAP-MSCHAPv2, EAP-GTC, EAP-TLS, EAP-PEAP-Public, EAP-PWD)
- TTLS (EAP-MSCHAPv2, EAP-GTC, EAP- TLS, EAP-MD5, PAP, CHAP)
- EAP-TLS
- PAP, CHAP, MSCHAPv1 and 2, EAP-MD5
- NAC, Microsoft NAP
- Windows machine authentication
- MAC auth
- Audit (rules based on port and vulnerability scans)
- Online Certificate Status Protocol (OCSP)
- SNMP generic MIB, SNMP private MIB
- Common Event Format (CEF), Log Event Extended Format (LEEF)
- TLS 1.2
|
| Supported identity stores |
- Microsoft Active Directory
- RADIUS
- Any LDAP compliant directory
- Any ODBC-compliant SQL server
- Token servers
- Built-in SQL store, static hosts list
- Kerberos
|
| RFC standards |
2246, 2248, 2548, 2759, 2865, 2866, 2869, 2882, 3079, 3576, 3579, 3580, 3748, 4017, 4137, 4849, 4851, 5216, 528, 7030 |
| Internet drafts |
Protected EAP Versions 0 and 1, Microsoft CHAP extensions, dynamic provisioning using EAP-FAST, TACACS+ |
| Information assurance validations |
FIPS 140-2 – Certificate #2577 |
| Profiling methods |
DHCP, TCP, MAC OUI, ClearPass Onboard, SNMP, Cisco device sensor |
| Appliance Specifications |
| CPU |
(1) Eight Core 2.4GHz Atom C2758 |
(1) Quad Core Xeon 3.4 GHz E3-1231_V3 |
(2) Six Core Xeon 2.4GHz E5-2620_V3 |
| Memory |
8 GB |
8 GB |
64 GB |
| Hard drive storage |
(1) SATA (7.3K RPM) 1TB hard drive |
(2) SATA (7.2K RPM) 1TB hard drives, RAID-1 controller |
(6) SAS (10K RPM) 600GB Hot-Plug hard drives, RAID-10 controller |
| Maximum devices |
500 |
5,000 |
25,000 |
Dimensions
(W x H x D) |
17.2” x 1.7” x 11.3” |
17.09” x 1.67” x 15.5” |
18.98” x 1.68” x 27.57” |
| Weight (max config) |
8.5 Lbs |
16.97 Lbs |
Up to 37 Lbs |
| Power supply |
200 watts max |
250 watts max |
750 watts max |
| Power redundancy |
N/A |
N/A |
optional |
| AC input voltage |
110/220 VAC auto-selecting |
110/220 VAC auto-selecting |
100/240 VAC auto-selecting |
| AC input frequency |
50/60 Hz auto-selecting |
50/60 Hz auto-selecting |
50/60 Hz auto-selecting |
| Operating temperature |
5º C to 35º C (41º F to 95º F) |
10º C to 35º C (50º F to 95º F) |
10º C to 35º C (50º F to 95º F) |
| Operating vibration |
0.25 G at 5 Hz to 200 Hz for 15 minutes |
0.26 G at 5 Hz to 350 Hz for 15 minutes |
0.26 G at 5 Hz to 350 Hz for 15 minutes |
| Operating shock |
1 shock pulse of 20 G for up to 2.5 ms |
1 shock pulse of 31 G for up to 2.6 ms |
1 shock pulse of 40 G for up to 2.3 ms |
| Operating altitude |
-16 m to 3,048 m
(-50 ft to 10,000 ft) |
-16 m to 3,048 m
(-50 ft to 10,000 ft) |
-16 m to 3,048 m
(-50 ft to 10,000 ft) |
* Virtual appliance sizing must match hardware appliance specifications



 Smart policies with mobility and IoT in mind
Smart policies with mobility and IoT in mind Futureproof your existing network infrastructure
Futureproof your existing network infrastructure
 One place to manage all things
One place to manage all things